Beware of Honeypot Scams in the Crypto World: How They Work, Characteristics, and Tips to Avoid Them
2025-10-16
Bittime - The ever-evolving blockchain world has also given rise to various new security threats. One increasingly popular method is the honeypot scam, a sophisticated form of fraud that utilizes fake smart contracts to trap investors. In a case that went viral in February 2024, a perpetrator managed to steal approximately $3.2 million through a series of honeypots on the network.Ethereum.
This article will thoroughly discuss what a honeypot scam is, how it works, the characteristics of malicious contracts, and the precautions you can take before investing in the crypto world.
READ ALSO:Who is Chen Zhi? The Man Behind the $15 Billion in Bitcoin Seized by the US Government
What Is a Honeypot Scam in Crypto
A honeypot scam is a malicious smart contract designed to appear profitable and legitimate to users, but actually contains hidden code that allows attackers to drain victims' funds.
Typically, these scams promise high returns, exclusive services, or rare opportunities for investors willing to deposit their crypto assets. However, when users try to withdraw their funds, they find their balances have been locked or completely lost.
Even experienced users can get caught out because honeypot scams often use complex contract mechanisms and convincing psychological manipulation.
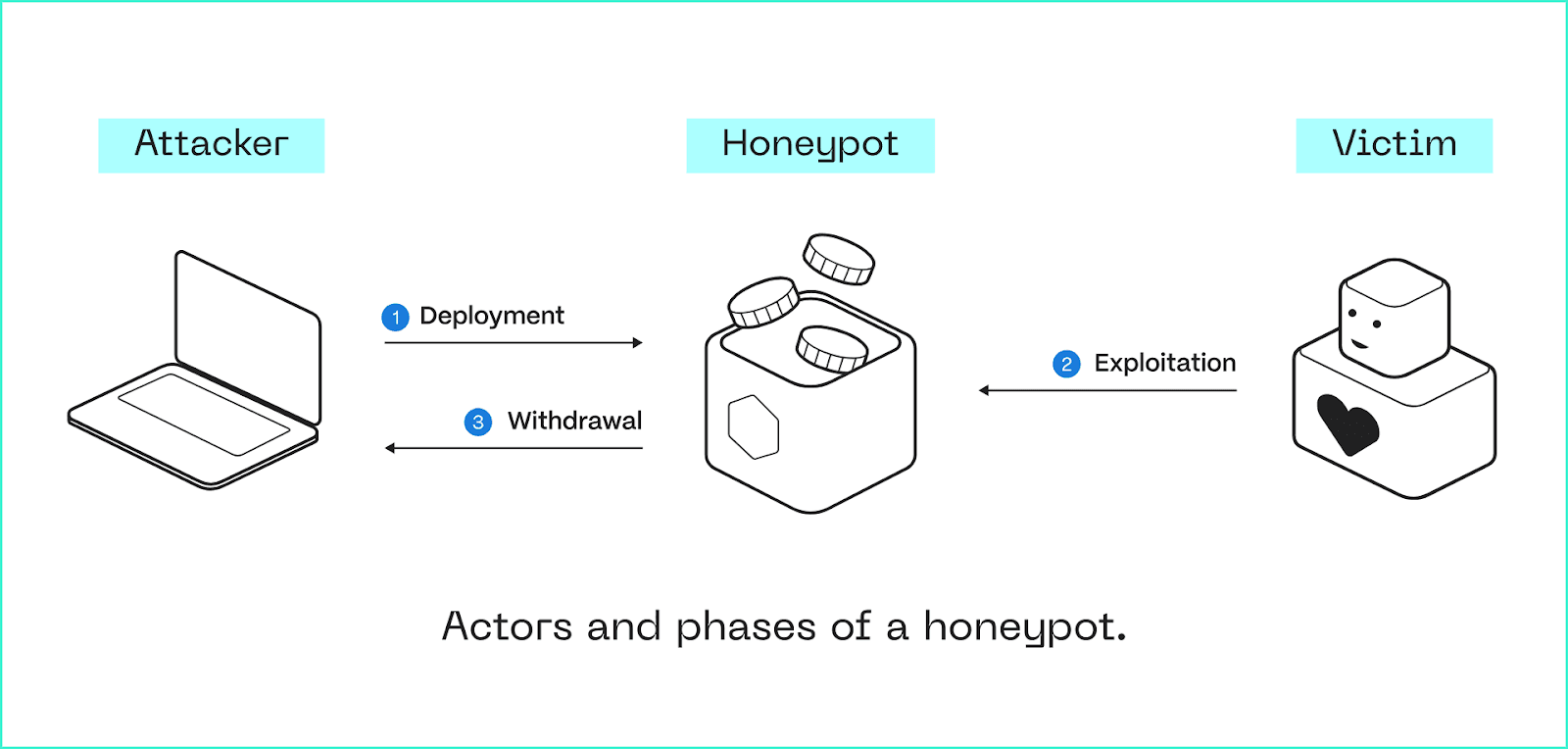
How Honeypot Scams Work on Blockchain
Honeypot scams usually follow a layered pattern:
Contract Development Stage: The fraudster creates a smart contract with malicious code that appears legitimate.
Promotion Stage: The project is marketed through social media, forums, and Telegram groups with promises of huge profits.
Exploitation Stage: Initially, transactions appear normal—small deposits and withdrawals are possible to build trust. However, when investors send large sums, a hidden mechanism locks the funds or transfers them directly to the perpetrator's wallet.
Obfuscation Stage: Attackers use fake accounts, paid actors, or proxy addresses to disguise their activity on the blockchain.
Some honeypot cases even involve sweeper bots, which are automated scripts that immediately move a victim's funds as soon as a transaction is made — much faster than a human can react.
Honeypot Scam Characteristics to Watch Out For
While they may seem complex, honeypot scams have identifiable patterns. Here are some signs to watch out for:
Contracts with “fake” vulnerabilitieswhich actually traps users who try to exploit it.
Withdrawals are limitedonly for certain addresses belonging to the attacker.
Fake transaction activity, such as artificial interactions between addresses controlled by scammers.
Misleading source code— for example, the withdrawal function appears to be active, but in fact cannot be executed.
Withdrawal time is limited (time lock) or inconsistent balancebetween the display and the actual value.
Not audited by a third partyand developed by an anonymous team with no clear identity.
Some examples of honeypots that have surfaced include the DeChat incident (2023) and the SHIB Telegram hack, both of which caused significant losses in the crypto community.
How to Avoid Honeypot Scams
Prevention is always better than regret. Here are some steps to avoid falling into a honeypot scam:
Cek audit smart contract.Avoid projects without audit reports from trusted parties.
Use a honeypot detection toolsuch as HoneyBadger, QuillCheck, or Token Sniffer.
Check transaction history on Etherscan.Be aware of suspicious activity such as failed withdrawals or funds being transferred immediately.
Research the development team.Anonymous teams or those without a digital footprint can be a red flag.
Follow trusted communities.Read reviews from independent sources and don't be easily swayed by exaggerated testimonials.
READ ALSO:South Korean Police Crack Down on GCV Crypto Scam
Conclusion
Honeypot scams are one of the biggest threats to the modern crypto ecosystem. This method not only exploits technical loopholes in smart contracts but also manipulates investors' psychology, trapping them in a state of greed and false trust.
By raising awareness, conducting your own research (DYOR), and only interacting with verified contracts, you can protect your digital assets from sophisticated traps like this.
How to Buy Crypto on Bittime
Want to trade sell buy BitcoinLooking for easy crypto investing? Bittime is here to help! As an Indonesian crypto exchange officially registered with Bappebti, Bittime ensures every transaction is secure and fast.
Start by registering and verifying your identity, then make a minimum deposit of IDR 10,000. After that, you can immediately purchase your favorite digital assets!
Check the course BTC to IDR, ETH to IDR, SOL to IDRand other crypto assets to find out today's crypto market trends in real-time on Bittime.
Additionally, visitBittime Blogto get various interesting updates and educational information about the world of crypto. Find trusted articles on Web3, blockchain technology, and digital asset investment tips designed to enrich your crypto knowledge.
FAQ
What is a honeypot scam in crypto?
Honeypot scam is a smart contract-based scam that tricks users into depositing funds but not being able to withdraw them.
How does a honeypot scam work?
Fraudsters make contracts appear legitimate and lock victims' funds through hidden codes.
Can honeypots be detected?
Yes, using tools like Token Sniffer or independent contract audits.
What are the signs of a potential honeypot project?
Limited withdrawals, fake transactions, and anonymous teams with no public audits.
How to protect yourself from honeypot scams?
Always do thorough research, use detection tools, and avoid unrealistic profit promises.
Disclaimer: The views expressed belong exclusively to the author and do not reflect the views of this platform. This platform and its affiliates disclaim any responsibility for the accuracy or suitability of the information provided. It is for informational purposes only and not intended as financial or investment advice.