What is Midnight (NIGHT)? Freedom Architecture is Rational Privacy
2026-01-14
What is Midnight (NIGHT)? Midnight is a cryptocurrency project that embraces the concept of the Architecture of Freedom and Rational Privacy. The project aims to give users more control over their privacy in the increasingly complex digital ecosystem.
By using the NIGHT token, Midnight focuses on security, decentralization, and transparency, allowing individuals to transact securely while maintaining their privacy freedom.
We will explore in depth how Midnight works, the NIGHT tokenomics, and the security of Midnight, as well as how the NIGHT token can become an essential privacy solution in the crypto world.
Key Takeaways
- Midnight (NIGHT) offers rational privacy in an increasingly connected digital world, giving users more control over their personal data.
- The NIGHT tokenomics supports decentralization and ensures a fair system, with transparent and well-structured token allocation.
- The security of Midnight is strengthened by independent audits and mechanisms that maintain the integrity of the system and transactions.
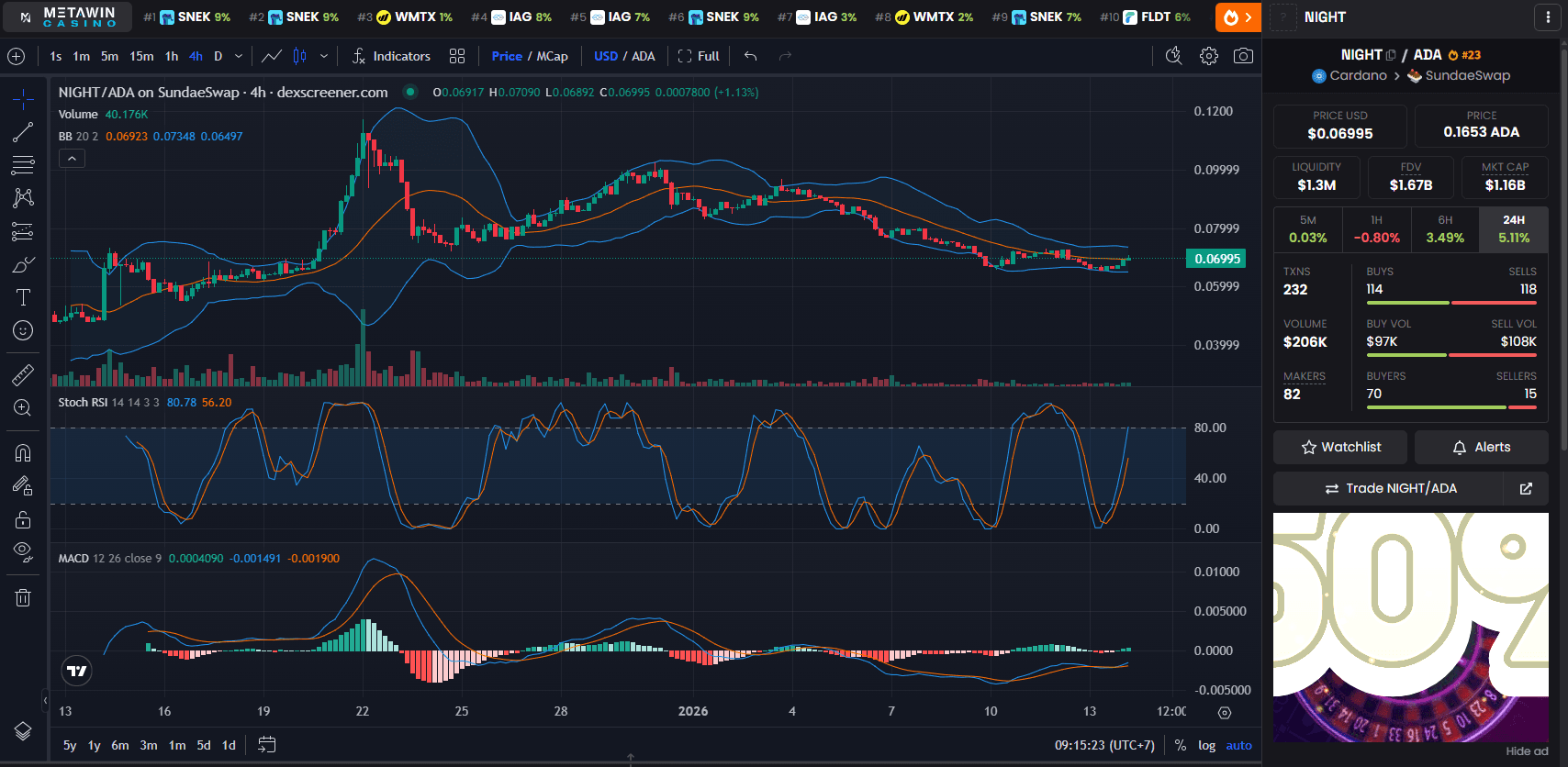
What is Midnight (NIGHT)?
Midnight (NIGHT) is a project focused on privacy and freedom. In an increasingly connected world, privacy is an important issue that is often overlooked, especially in digital transactions.
Midnight comes as a solution that gives individuals greater control over their data, ensuring that only they have the right to access personal information.
The concept of "rational privacy" promoted by Midnight is not only about protecting data, but also enabling privacy to be maintained without compromising functionality or user transaction convenience.
The NIGHT token is at the core of the Midnight ecosystem. This token is used to transact on the network and gain access to various features provided by the platform. Whether for personal transactions, smart contracts, or even staking, the NIGHT token plays a crucial role in maintaining user privacy.
Also Read: 7 Effective Crypto Trading Tips for Beginners, Complete with Tips and Tricks
The Architecture of Midnight Freedom
This project brings a vision to create a decentralized ecosystem that gives freedom to its users, with full control over their personal data.
One of the key pillars of this architecture is the transparent and accessible NIGHT audit, ensuring that every transaction made is secure and in line with the privacy principles applied.
- Decentralization: Eliminating reliance on centralized entities that are often data breach targets.
- Rational Privacy: Balancing privacy and freedom without restricting app functionality or user transactions.
- Security: Ensuring network integrity with encryption systems and independent audits.
How Does Midnight (NIGHT) Work?
Midnight works by creating a secure and transparent environment for its users. Every transaction and data processed through the Midnight network is tightly protected with strong encryption, allowing only authorized parties to access certain information.
The decentralized system in use allows transaction verification directly by the network without relying on a central authority.
One important component of this network is the NIGHT token, which is used for various activities within the ecosystem. This includes payments for services, participation in the consensus mechanism, and as an incentive for network participants to maintain integrity and security.
- Privacy and Anonymity: Users can transact with high levels of privacy, ensuring personal data is not leaked to third parties.
- Decentralization: Reducing the risk of centralized attacks and giving full control to users.
- Consensus Mechanism: Supporting transaction validation through an efficient and fair system, without the need for a trusted third party.
Token Allocation: NIGHT Tokenomics
NIGHT tokenomics ensures that the distribution of tokens is done fairly and transparently. As the network develops, NIGHT tokens are allocated for various purposes, such as incentives for validators, project development, and ecosystem support.
The project strives to maintain a balance between community involvement and network economic growth.
The project also ensures that token allocation is done in a way that is not too centralized, meaning most tokens are available to the public.
With a transparent tokenomics model, the NIGHT token is expected to grow organically and attract more users into the network.
- Balanced Allocation: Tokens available for project development, validator incentives, and community participation.
- Community Involvement: Giving the community the opportunity to participate in the development and sustainability of the project.
- Network Economic Growth: Supporting a healthy ecosystem with proper incentives for all parties involved.
Also Read: Crypto Trading Strategies for Beginners, Don't Do This!
Midnight Security and NIGHT Audit
Security is a key aspect of Midnight crypto. The network is designed with multiple layers of protection to safeguard users' data and transactions. One of the main features of Midnight's security is the use of transparent and independent audit systems.
This ensures that every transaction made through the network can be verified by anyone, maintaining integrity and reducing the potential for errors or manipulation.
The NIGHT audit is conducted regularly by independent third parties to ensure that no security vulnerabilities exist in the system.
In this way, users can feel safe and trust that their data is well protected, even in an open digital environment.
- Independent Audit: Ensures that every part of the network is audited for potential security breaches.
- Advanced Encryption: Users' data is protected with strong encryption, only accessible by authorized parties.
- Transparency and Security: Ensures no one can manipulate transactions or user data.
Conclusion
With a strong vision for rational privacy and user freedom, Midnight (NIGHT) offers an innovative solution in the crypto world that increasingly emphasizes transparency and decentralization.
By combining balanced NIGHT tokenomics, reliable Midnight security, and independent NIGHT audit systems, Midnight is ready to become a key player in the crypto ecosystem focused on privacy.
If you are interested in trading NIGHT tokens or want to read more about the world of crypto, you can visit Bittime Exchange or read interesting articles on Bittime Blog.
FAQ
What is Midnight (NIGHT)?
Midnight is a crypto project aimed at providing privacy and digital freedom to its users through the use of NIGHT token.
How does Midnight work?
Midnight works with a decentralized system and encryption to ensure transactions are secure and users' privacy is protected.
What is NIGHT token?
NIGHT token is the utility token within the Midnight ecosystem, used for transactions and staking on the network.
How does NIGHT tokenomics support network growth?
NIGHT tokenomics distributes tokens fairly for project development, validator incentives, and community participation.
Why is NIGHT audit important?
NIGHT audit ensures transparency and network security by checking each transaction to identify potential vulnerabilities or manipulation.
How to Buy Crypto on Bittime?
Want to trade or buy buy Bitcoin and invest in crypto easily? Bittime is ready to help! As an officially registered crypto exchange in Indonesia under Bappebti, Bittime ensures every transaction is safe and fast.
Start by registering and verifying your identity, then make a minimum deposit of Rp10,000. After that, you can immediately buy your favorite digital assets!
Check the exchange rates BTC to IDR, ETH to IDR, SOL to IDR and other crypto assets to find out the crypto market trends today in real-time on Bittime.
Additionally, visit Bittime Blog to get various interesting updates and educational information about the crypto world. Find trustworthy articles on Web3, blockchain technology, and digital asset investment tips designed to enrich your knowledge of the crypto world.
Disclaimer: The views expressed belong exclusively to the author and do not reflect the views of this platform. This platform and its affiliates disclaim any responsibility for the accuracy or suitability of the information provided. It is for informational purposes only and not intended as financial or investment advice.